Gestión de DNS en Azure con Terraform: Implementación y Automatización
Introducción
La gestión eficiente del DNS es crucial para cualquier infraestructura en la nube. En este artículo, exploraremos cómo implementar y gestionar Azure DNS utilizando Terraform, incluyendo configuraciones avanzadas y mejores prácticas.
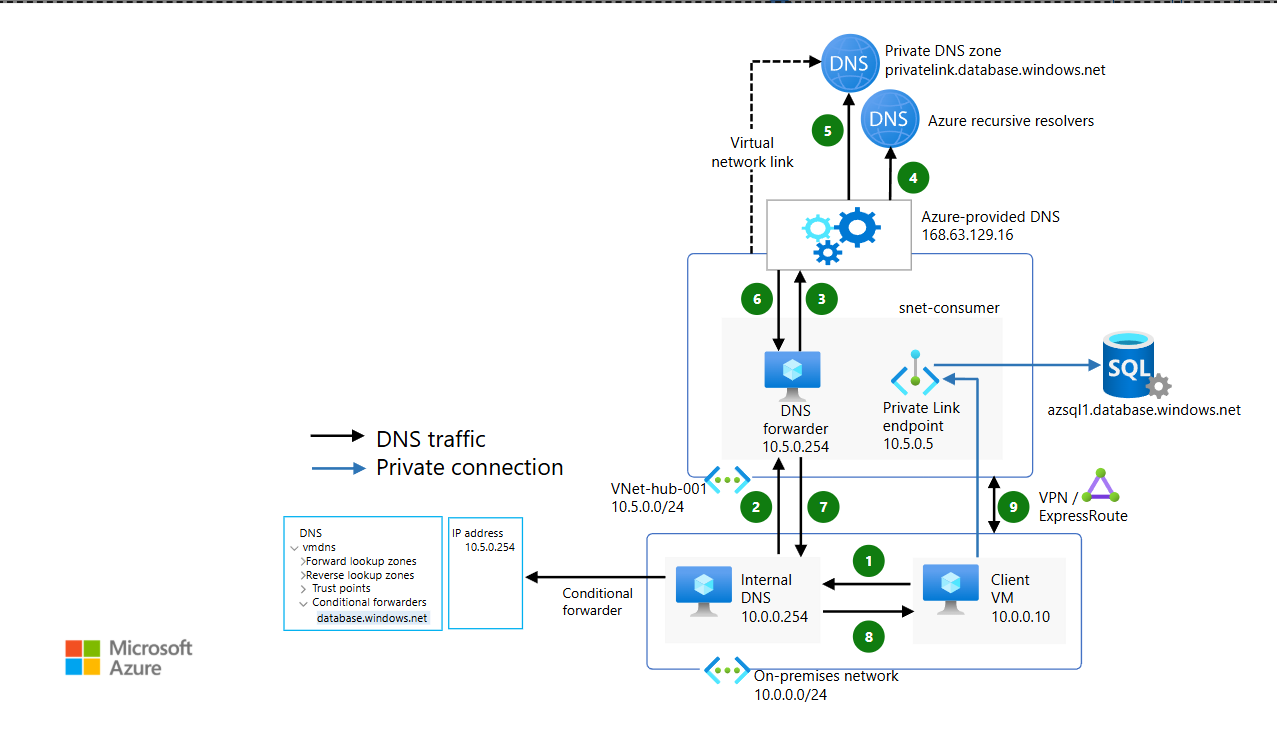
Configuración de Zona DNS
# Crear una zona DNS pública
resource "azurerm_dns_zone" "public" {
name = "example.com"
resource_group_name = azurerm_resource_group.main.name
tags = {
environment = "Production"
managed_by = "Terraform"
}
}
# Crear una zona DNS privada
resource "azurerm_private_dns_zone" "private" {
name = "internal.example.com"
resource_group_name = azurerm_resource_group.main.name
tags = {
environment = "Production"
type = "Private"
}
}
Registros DNS Comunes
# Registro A
resource "azurerm_dns_a_record" "www" {
name = "www"
zone_name = azurerm_dns_zone.public.name
resource_group_name = azurerm_resource_group.main.name
ttl = 300
records = ["203.0.113.1"]
}
# Registro CNAME
resource "azurerm_dns_cname_record" "app" {
name = "app"
zone_name = azurerm_dns_zone.public.name
resource_group_name = azurerm_resource_group.main.name
ttl = 300
record = "www.example.com"
}
# Registro MX
resource "azurerm_dns_mx_record" "mail" {
name = "@"
zone_name = azurerm_dns_zone.public.name
resource_group_name = azurerm_resource_group.main.name
ttl = 300
record {
preference = 10
exchange = "mail1.example.com"
}
record {
preference = 20
exchange = "mail2.example.com"
}
}
Integración con Redes Virtuales
# Vincular zona DNS privada con VNet
resource "azurerm_private_dns_zone_virtual_network_link" "example" {
name = "vnet-link"
resource_group_name = azurerm_resource_group.main.name
private_dns_zone_name = azurerm_private_dns_zone.private.name
virtual_network_id = azurerm_virtual_network.main.id
registration_enabled = true
}
Configuración de Azure Front Door con DNS
resource "azurerm_frontdoor" "example" {
name = "example-frontdoor"
resource_group_name = azurerm_resource_group.main.name
routing_rule {
name = "exampleRoutingRule1"
accepted_protocols = ["Http", "Https"]
patterns_to_match = ["/*"]
frontend_endpoints = ["exampleFrontendEndpoint1"]
forwarding_configuration {
forwarding_protocol = "MatchRequest"
backend_pool_name = "exampleBackendPool"
}
}
backend_pool {
name = "exampleBackendPool"
backend {
host_header = "www.example.com"
address = "www.example.com"
http_port = 80
https_port = 443
}
}
frontend_endpoint {
name = "exampleFrontendEndpoint1"
host_name = "example-frontdoor.azurefd.net"
custom_https_provisioning_enabled = false
}
}
# DNS CNAME para Front Door
resource "azurerm_dns_cname_record" "frontdoor" {
name = "fd"
zone_name = azurerm_dns_zone.public.name
resource_group_name = azurerm_resource_group.main.name
ttl = 300
record = azurerm_frontdoor.example.frontend_endpoints[0].host_name
}
Gestión de Certificados SSL
resource "azurerm_dns_txt_record" "verification" {
name = "@"
zone_name = azurerm_dns_zone.public.name
resource_group_name = azurerm_resource_group.main.name
ttl = 300
record {
value = "MS=ms123456789"
}
}
Monitorización y Alertas
resource "azurerm_monitor_activity_log_alert" "dns_changes" {
name = "dns-changes-alert"
resource_group_name = azurerm_resource_group.main.name
scopes = [azurerm_dns_zone.public.id]
description = "Alert when DNS changes occur"
criteria {
category = "Administrative"
resource_type = "Microsoft.Network/dnszones"
operation_name = "Microsoft.Network/dnszones/*/write"
}
action {
action_group_id = azurerm_monitor_action_group.example.id
}
}
Recuperación ante Desastres
# Zona DNS secundaria en otra región
resource "azurerm_dns_zone" "secondary" {
name = "example.com"
resource_group_name = azurerm_resource_group.dr.name
tags = {
environment = "DR"
type = "Secondary"
}
}
# Replicación de registros
resource "azurerm_dns_a_record" "www_dr" {
name = "www"
zone_name = azurerm_dns_zone.secondary.name
resource_group_name = azurerm_resource_group.dr.name
ttl = 300
records = ["203.0.113.2"]
}
